Microsoft released an introduction video to Azure Bastion a couple of days ago and today a new post has gone live giving us all the details of Azure Bastion in its preview state.
First up, what is a Bastion? Often referred to as a jumpbox, jumphost or bastion host, it’s a server which provides access to a private network from an external network, most commonly the Internet. As it’s exposed to potential attack, bastion hosts must be designed to minimize risk of penetration. As this connectivity function is so widely used, bastions are quite common in the majority of environments. The alternative is to increase your perimeter exposure by allowing public access to your private resources directly. Little tip from me, please don’t do this!
However, management and administration of these hosts can be a complex and time consuming task. Thankfully, Microsoft have introduced a new PaaS based service – Azure Bastion. Which allows managed, seamless access to VMs in your private network via RDP and SSH over SSL.

Azure Bastion is provisioned directly into a virtual network, which allows bastion host and integrated connectivity to all virtual machines within that vnet using RDP/SSH directly from and through your browser via the Azure Portal.
Microsoft list the following as key features available right now as part of the preview:
- RDP and SSH from the Azure portal: Initiate RDP and SSH sessions directly in the Azure portal with a single-click seamless experience.
- Remote session over SSL and firewall traversal for RDP/SSH: HTML5 based web clients are automatically streamed to your local device providing the RDP/SSH session over SSL on port 443. This allows easy and securely traversal of corporate firewalls.
- No public IP required on Azure Virtual Machines: Azure Bastion opens the RDP/SSH connection to your Azure virtual machine using a private IP, limiting exposure of your infrastructure to the public Internet.
- Simplified secure rules management: Simple one-time configuration of Network Security Groups (NSGs) to allow RDP/SSH from only Azure Bastion.
- Increased protection against port scanning: The limited exposure of virtual machines to the public Internet will help protect against threats, such as external port scanning.
- Hardening in one place to protect against zero-day exploits: Azure Bastion is a managed service maintained by Microsoft. It’s continuously hardened by automatically patching and keeping up to date against known vulnerabilities.
And they list the following as on the roadmap for future release:
The future brings Azure Active Directory integration, adding seamless single-sign-on capabilities using Azure Active Directory identities and Azure Multi-Factor Authentication, and effectively extending two-factor authentication to your RDP/SSH connections. We are also looking to add support for native RDP/SSH clients so that you can use your favorite client applications to securely connect to your Azure Virtual Machines using Azure Bastion, while at the same time enhance the auditing experience for RDP sessions with full session video recording.
There are a couple of things to note as the service is in preview. As always, be wary deploying for production, there is no SLA yet.
The preview is limited to the following Azure public regions:
- West US
- East US
- West Europe
- South Central US
- Australia East
- Japan East
You have to register the resource provider manually to make use of the preview, instructions on how to do that here.
To use the Azure Bastion service, you need the following roles:
- Reader role on the virtual machine
- Reader role on the NIC with private IP of the virtual machine
- Reader role on the Azure Bastion resource
Once you’re OK with all of the above, you can simply click connect on any of your VM resources and a new Bastion tab is available. From here you can launch your session to the VM right in the browser, which is pretty slick as it provides copy and paste and full screen functionality already.
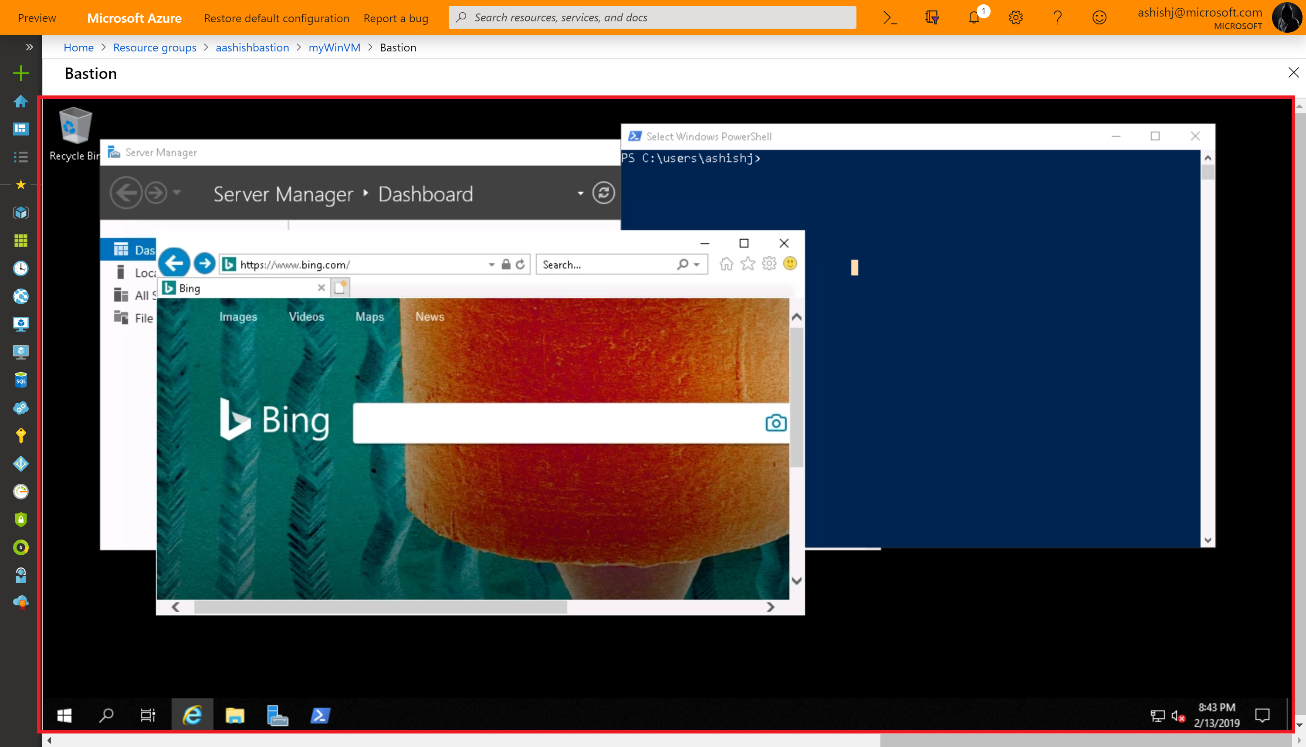
One item I noticed from the FAQ is that you may need to use the preview link to access the resource deployment blade from the portal – https://aka.ms/BastionHost
Also of note, pricing! On the FAQ it states you will be billed partially. Not 100% sure what that means, so watch those usage rates. The pricing page is live however so check it out in advance here.





