This month, Microsoft announced the introduction of a new method of running your Windows and Linux VMs within Azure. Dedicated Host is a new service that provides you with a single-tenant-host to run your workloads on. Or to phrase that more simply, your very own physical server in an Azure datacentre.
Azure Dedicated Host Groups (DHG) can be created within a region, availability zone, and fault domain. Your Dedicated Host is then created as part of a DHG and you can have multiple Dedicated Hosts per DHG. A Dedicated Host is a representation of a physical server in an Azure Datacenter. As your VMs are directly provisioned into your hosts, you can choose whatever configuration is required and available from the parent resources.

Two benefits from making use of Dedicated Host are:
Increased Control
As your Dedicated Host is allocated directly to your tenant, you have more granular control of placement configuration for all of your provisioned VMs. Also, you now control the timing of all platform-initiated maintenance operations, such as OS patching, or hardware or software reboots. This means you get the option to skip the regular platform update schedule, and then apply it when it suits within a 35-day rolling window.
Compliance Requirements
Azure Dedicated Host offers hardware isolation at the physical level which means your Azure VMs run on an isolated and dedicated physical server. No other VMs can run on your Dedicated Host. This can drastically help meet corporate compliance guidelines and standards. While also gaining visibility into the underlying cores to meet server-based software licensing requirements.
Configuration Options
Dedicated Hosts come in several configuration options. Each options allow for different VM series deployment combinations you are already familiar with. A table outlines an example for the Dsv3 Series:
| Physical Cores | Available vCPUs | Available RAM | VM Size | # of VMs |
| 40 | 64 | 256GB | D2s v3 D4s v3 D8s v3 D16s v3 D32s v3 D48s v3 D64s v3 | 32 16 8 4 2 1 1 |
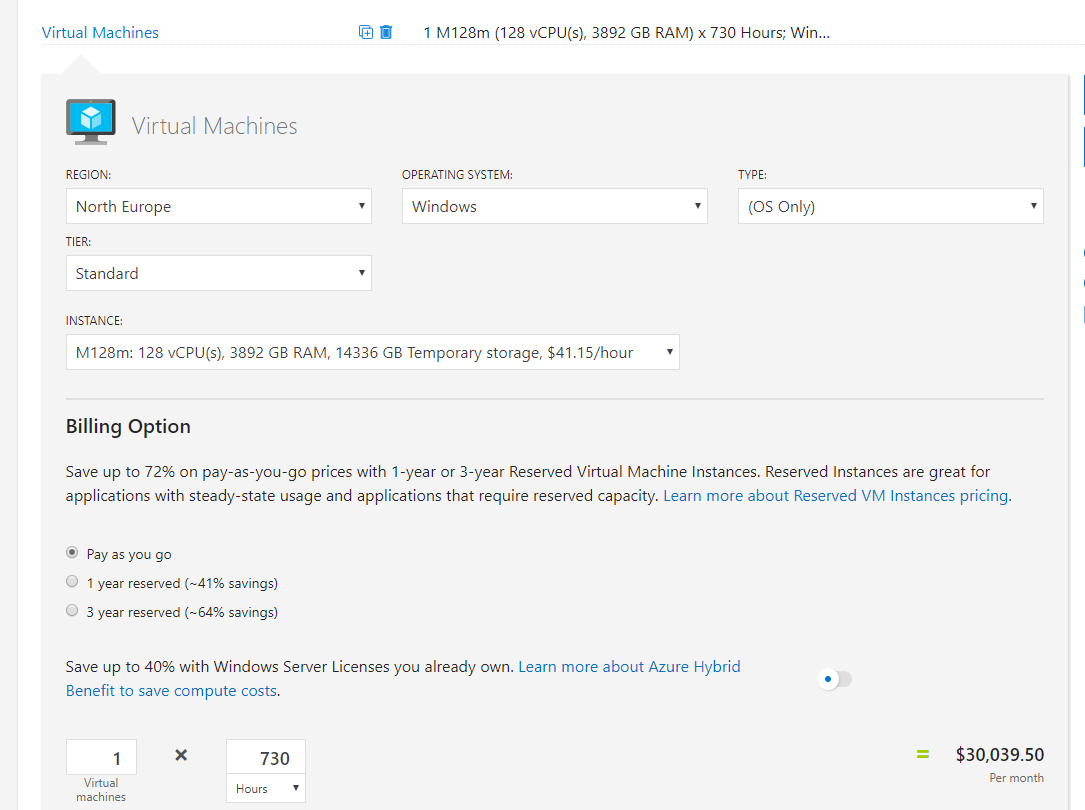
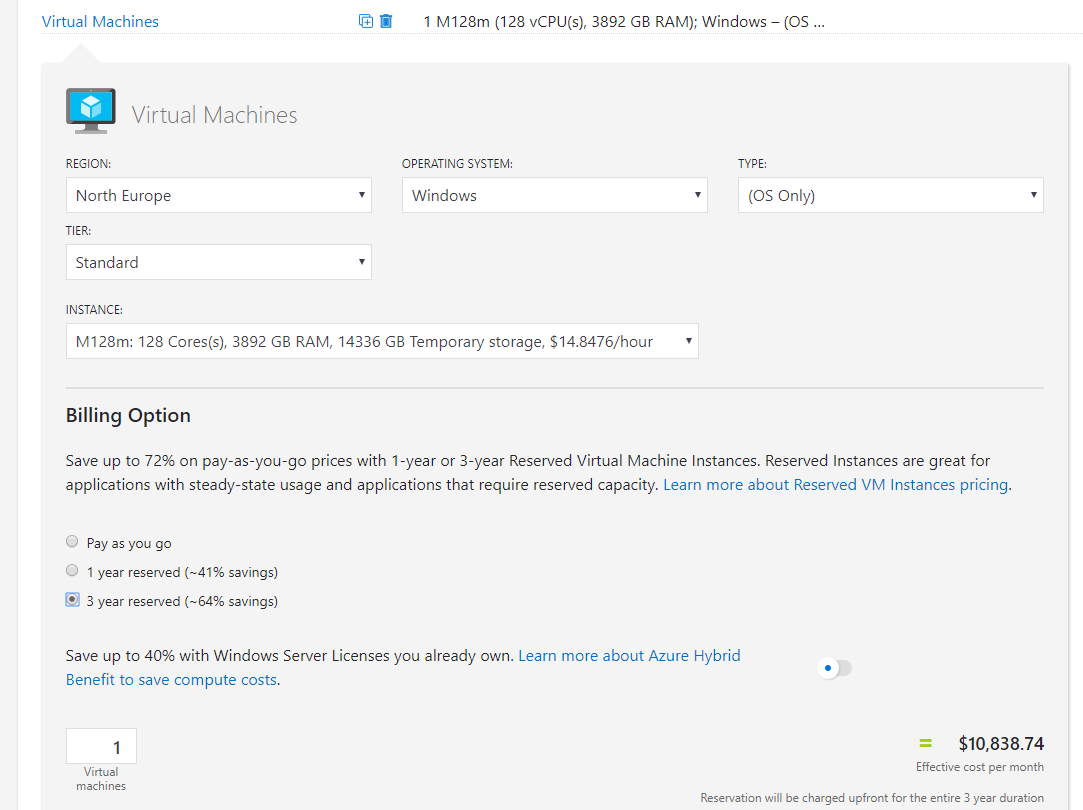
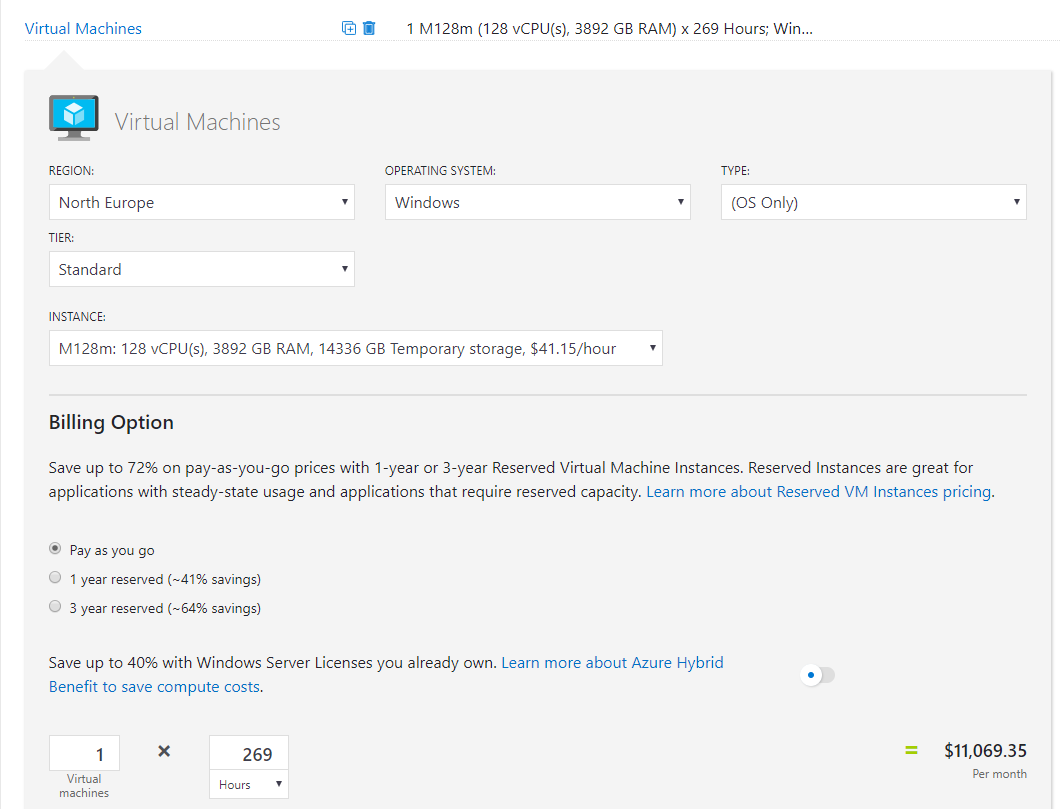
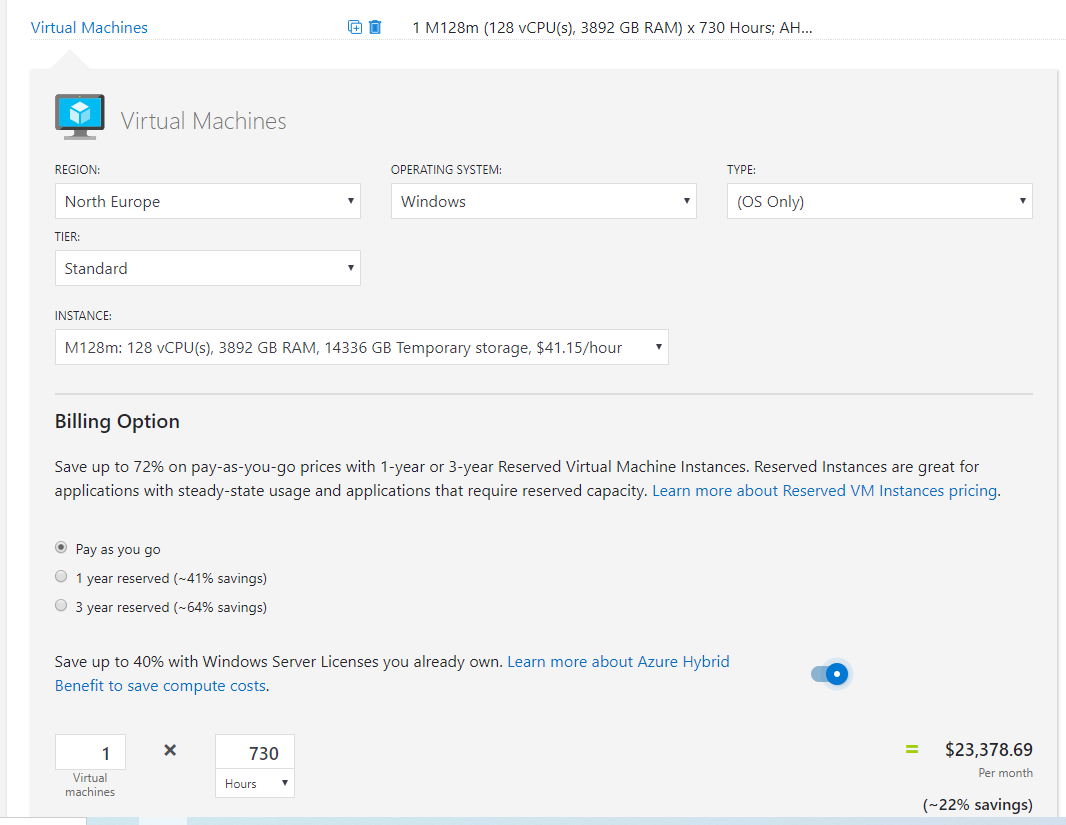
So at a quick glance, you can see there are several combinations of VMs that can be run on any single Dedicated Host. For example, 2 D16s v3 VMs + 1 D32s v3 VMs. However, bear in mind you will pay for the full Dedicated Host, regardless of VMs being run on it. You can read the full details for more information on pricing.
One nice note on pricing; the usual Azure Hybrid Benefit options are available for VMs running on Dedicated Host.
DHGs use Availability Zones and Fault Domains to give the greatest High Availability possible. So both need to be taken into consideration when designing your Dedicated Host deployment. The Dedicated Host docs, give good guidance on this already.
If Dedicated Host sounds like something you could make use of, why not give it a try. But remember, it’s still in preview so be careful and be aware of the limitations below:
- Virtual machine scale sets are not currently supported on dedicated hosts.
- The preview initial release supports the following VM series: DSv3 and ESv3.
- During the preview, you won’t be able to resize a virtual machine deployed to a dedicated host.
- Control over maintenance capabilities is in a limited preview. Start by taking this nomination survey to try them out.
- During the preview we won’t be offering the option for reserved capacity.